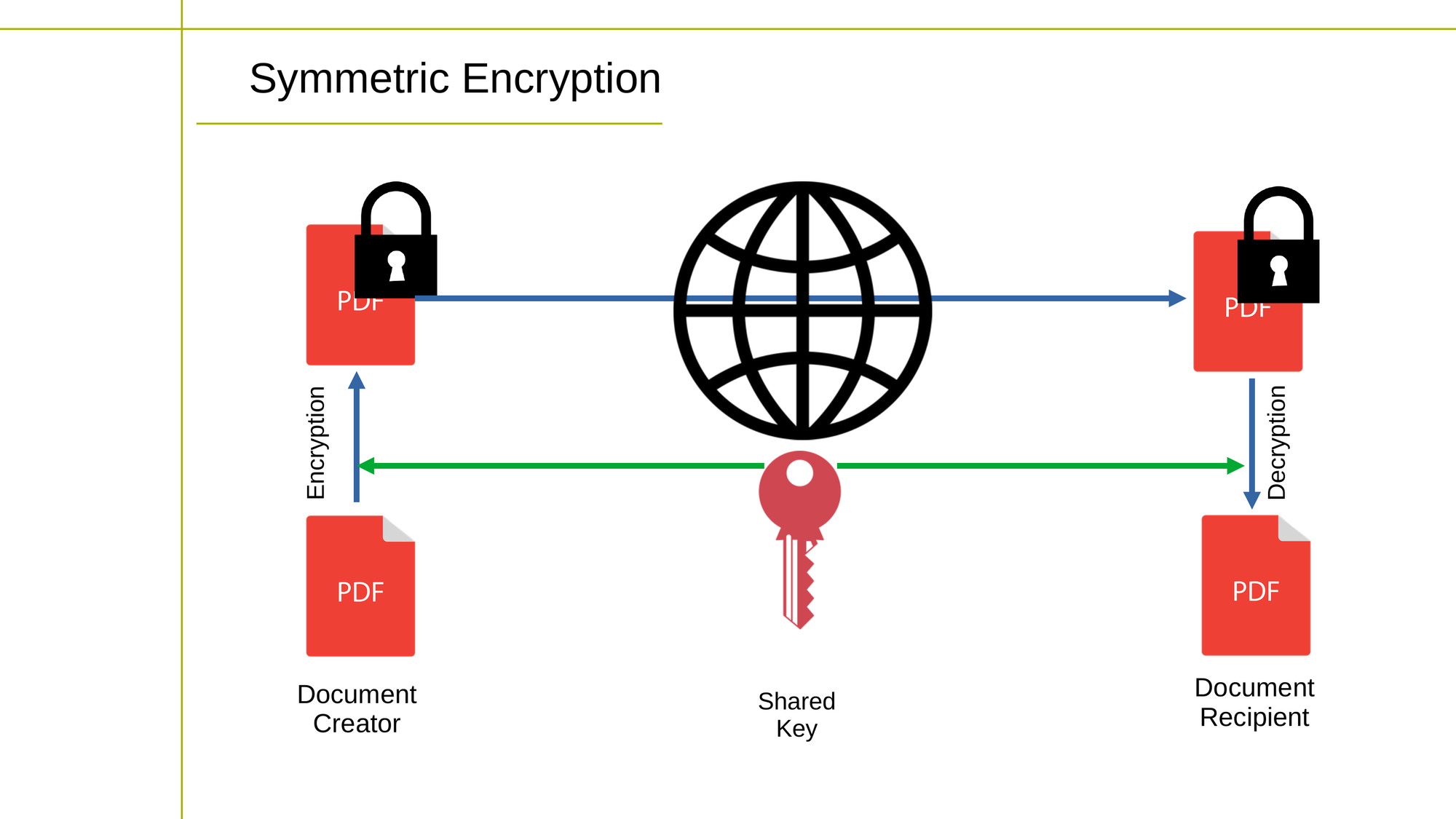
Explain The Problems With Key Management And How It Affects Symmetric Cryptography . key management and distribution: In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. Both the sender and the receiver in the skc of a message need to have the same key, and the key. key management, or encryption key management, is the process of generating, exchanging, storing and managing. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric.
from www.freecodecamp.org
we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. key management and distribution: Both the sender and the receiver in the skc of a message need to have the same key, and the key. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. key management, or encryption key management, is the process of generating, exchanging, storing and managing.
What is Encryption at Rest? Explained for Security Beginners
Explain The Problems With Key Management And How It Affects Symmetric Cryptography Both the sender and the receiver in the skc of a message need to have the same key, and the key. Both the sender and the receiver in the skc of a message need to have the same key, and the key. key management and distribution: we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. key management, or encryption key management, is the process of generating, exchanging, storing and managing.
From www.freecodecamp.org
What is Encryption at Rest? Explained for Security Beginners Explain The Problems With Key Management And How It Affects Symmetric Cryptography key management and distribution: key management, or encryption key management, is the process of generating, exchanging, storing and managing. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. Both the sender and the receiver. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.slideserve.com
PPT Symmetric Key Cryptography PowerPoint Presentation, free download ID1720093 Explain The Problems With Key Management And How It Affects Symmetric Cryptography In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. key management, or encryption key management, is the process of generating, exchanging, storing and managing. we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. Both the sender and the receiver in. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.youtube.com
Module 5 What is symmetric key encryption? YouTube Explain The Problems With Key Management And How It Affects Symmetric Cryptography key management, or encryption key management, is the process of generating, exchanging, storing and managing. key management and distribution: Both the sender and the receiver in the skc of a message need to have the same key, and the key. we discuss the choosing of key lengths and look at different techniques for key generation, including key. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.thesslstore.com
Symmetric Encryption 101 Definition, How It Works & When It’s Used Hashed Out by The SSL Store™ Explain The Problems With Key Management And How It Affects Symmetric Cryptography Both the sender and the receiver in the skc of a message need to have the same key, and the key. key management and distribution: In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. . Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.mybscit.com
Explain Symmetric and Asymmetric key cryptography together Explain The Problems With Key Management And How It Affects Symmetric Cryptography Both the sender and the receiver in the skc of a message need to have the same key, and the key. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. key management, or encryption key. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.researchgate.net
Symmetric key cryptography process Download Scientific Diagram Explain The Problems With Key Management And How It Affects Symmetric Cryptography key management, or encryption key management, is the process of generating, exchanging, storing and managing. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. we discuss the choosing of key lengths and look at. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.slideserve.com
PPT Chapter 8 Network Security Principles, Symmetric Key Cryptography, Public Key Cryptography Explain The Problems With Key Management And How It Affects Symmetric Cryptography key management and distribution: Both the sender and the receiver in the skc of a message need to have the same key, and the key. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. key management, or encryption key management, is the process of generating, exchanging, storing and managing. we discuss. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From o3schools.com
Ultimate Guide to Understanding What Symmetric Key Cryptography is 2023 Explain The Problems With Key Management And How It Affects Symmetric Cryptography we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. key management and distribution: In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. key management, or encryption key management, is the process of generating, exchanging, storing and managing. Both the. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From blockgeeks.com
Learn All About Cryptocurrencies Cryptography because it Works! Explain The Problems With Key Management And How It Affects Symmetric Cryptography key management, or encryption key management, is the process of generating, exchanging, storing and managing. key management and distribution: In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. we discuss the choosing of. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.chegg.com
Solved 15.8 Explain the problems with key management and Explain The Problems With Key Management And How It Affects Symmetric Cryptography this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. Both the sender and the receiver in the skc of a message need to have the same key, and the key. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. we discuss the choosing of. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.slideserve.com
PPT Lecture 02 Symmetric Cryptography PowerPoint Presentation, free download ID1402096 Explain The Problems With Key Management And How It Affects Symmetric Cryptography we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. Both the sender and the receiver in the skc of a message need to have the same key, and the key. this article explains important things about key exhaustion, rotation, and security models in the context of. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From cybermeteoroid.com
Symmetric And Asymmetric Cryptography Which One is Secure ? cybermeteoroid Explain The Problems With Key Management And How It Affects Symmetric Cryptography key management, or encryption key management, is the process of generating, exchanging, storing and managing. this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. Both the sender and the receiver in the skc of a message need to have the same key, and the key. In asymmetric keys, a pair. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From t0o0tz.com
Symmetric Key Cryptography at a Glance Explain The Problems With Key Management And How It Affects Symmetric Cryptography this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. key management and distribution: we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data.. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.mybscit.com
Explain Symmetric and Asymmetric key cryptography together Explain The Problems With Key Management And How It Affects Symmetric Cryptography Both the sender and the receiver in the skc of a message need to have the same key, and the key. key management, or encryption key management, is the process of generating, exchanging, storing and managing. key management and distribution: In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. this article. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From doubleoctopus.com
What is Symmetric Key Cryptography Encryption? Security Wiki Explain The Problems With Key Management And How It Affects Symmetric Cryptography In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. key management and distribution: Both the sender and the receiver in the skc of a message need to have the same key, and the key. we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.slideserve.com
PPT symmetric key cryptography PowerPoint Presentation, free download ID5597777 Explain The Problems With Key Management And How It Affects Symmetric Cryptography this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. key management, or encryption key management, is the process of generating, exchanging, storing and managing. key management and distribution: In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. we discuss the choosing of. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.webopedia.com
What is Symmetric Encryption? Symmetric Cryptography opedia Explain The Problems With Key Management And How It Affects Symmetric Cryptography this article explains important things about key exhaustion, rotation, and security models in the context of symmetric. Both the sender and the receiver in the skc of a message need to have the same key, and the key. key management, or encryption key management, is the process of generating, exchanging, storing and managing. we discuss the choosing. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.
From www.slideserve.com
PPT Network Security Principles, Symmetric Key Cryptography, Public Key Cryptography Explain The Problems With Key Management And How It Affects Symmetric Cryptography key management, or encryption key management, is the process of generating, exchanging, storing and managing. we discuss the choosing of key lengths and look at different techniques for key generation, including key derivation and generation from. In asymmetric keys, a pair of keys are used to encrypt and decrypt the data. Both the sender and the receiver in. Explain The Problems With Key Management And How It Affects Symmetric Cryptography.